It is no longer possible to imagine the Internet without SSL certificates. They are mandatory for websites if login data, passwords or personal data are transmitted in any form. They signal to visitors that their data is being transmitted in encrypted form, and in the case of certificates with Company Validation or Extended Validation, they can see for which company they have been issued.
How is it ensured that an SSL certificate was actually requested by the very company on whose website it is installed? For a fraudster who, for example, wants to redirect visitors of a bank to a fake website, it would of course be a great help if he could also show the SSL certificate of the bank on his website! To prevent this, every public certificate issuer (Certificate Authority) checks the authenticity of the applicant through validation . In the past, this validation has not always worked one hundred percent. The best-known case: Symantec issued certificates for google.com without authorisation in the past (whereupon Google withdrew its trust in Symantec and its subsidiaries).
As a browser manufacturer, Google naturally has a powerful means of withdrawing trust from a certificate issuer: Google only has to teach its browser to display the error message Untrusted! for all such certificates. Only a few people have this option. But what can a normal certificate user do to defend himself against the unauthorised issuing of a certificate for his domain?
One preventive possibility is to specify in the DNS of one's domain which certificate issuer one would like to allow to issue SSL certificates for this domain. This can be achieved through so-called CAA records. Here is an example in the DNS editor at deLink:
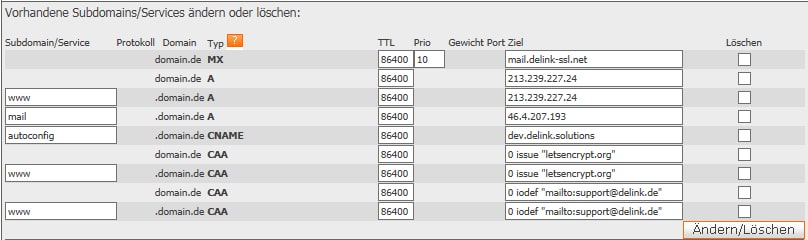
The entry
domain.de CAA 0 issue "letsenrypt.org"
states that only the certificate issuer Let's Encrypt should be authorised to issue SSL certificates for domain.de. The entry
domain.de CAA 0 iodef "mailto:support@delink.de"
states that all other certificate issuers should send an email to support@delink.de when an SSL certificate for domain.de is requested from them. The same should apply to www.domain.de. By entering
domain.de CAA 0 issuewild "letsencrypt.org"
one can also specify that the authorisation should apply to the domain and all its subdomains. A list with the names of the available certificate issuers is maintained by Mozilla, among others.
It should be noted that CAA records are only recommendations to the public certificate issuers. The future will show to what extent the issuers adhere to them. In any case, CAA records represent a certain, albeit not absolute, protection against the unauthorised issuing of certificates. In the case of important domains, this protection option should not be missed.
